
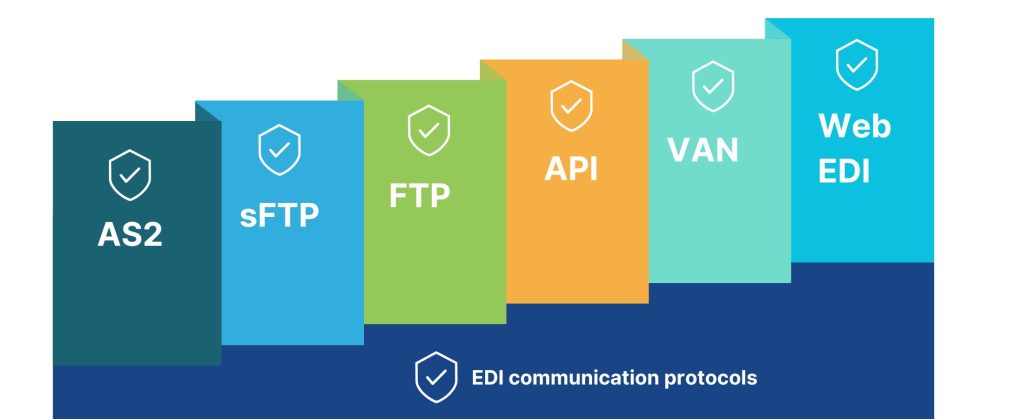
Today many companies, be they small-scale firms or medium to large-scale industries are adopting the use of EDI technology to streamline their communication process. EDI helps exchange business documents between organizations via the use of communication protocols.
Think of EDI protocols as a software language like HTML, JavaScript, or any other computer language. EDI protocols are software formats used for sending and receiving data. These protocols define how the EDI data is transmitted, authenticated, and secured during transmission. To exchange EDI data successfully businesses must use the same EDI protocols at both ends unless the businesses are using a third-party VAN provider that acts as a middleman, translating EDI messages between protocols and partners while enabling you to use your own, single protocol no matter which protocols your partner use.
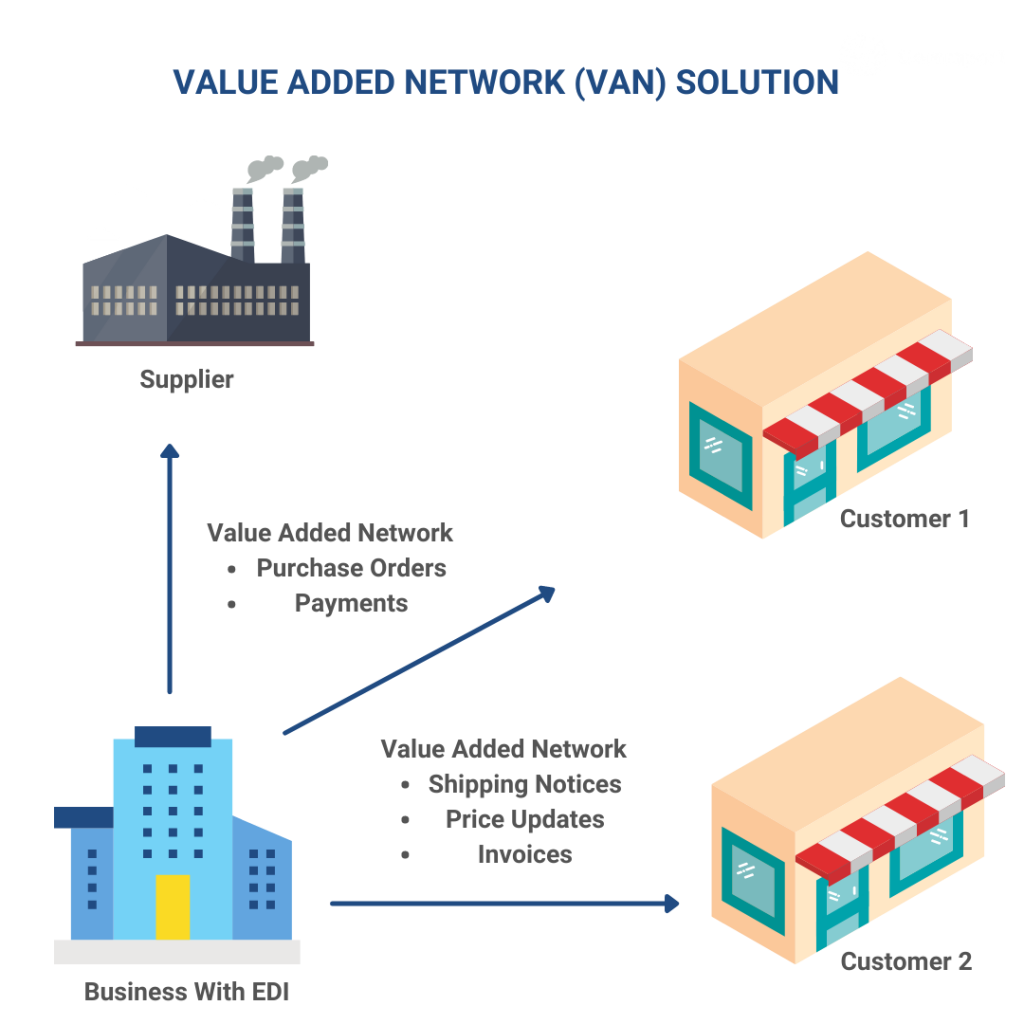
A VAN is a third-party service provider that acts as a hub to facilitate EDI data transmission between trading partners. The VAN provides the infrastructure, security, and support needed to transmit EDI data between partners. VAN also provides evidence of the delivery and processing of EDI messages at the destination. The advantage of using a 3rd party VAN is it acts as a middleman, translating EDI messages between protocols and partners while enabling you to use your own, single protocol no matter which protocols your partner uses.
A VAN provides a high level of security for EDI data transmission, including encryption, authentication, and access controls. This ensures that EDI data is transmitted securely and is only accessible to authorized parties.
It offers a reliable and stable EDI communication infrastructure, with redundant systems, backup mechanisms, and disaster recovery plans in place to ensure uninterrupted EDI data transmission.
Using a VAN can be cost-effective for companies that need to exchange EDI data with multiple partners, as it eliminates the need to establish individual point-to-point connections with each partner.
A VAN can simplify the onboarding process for new trading partners, as the VAN provides a single connection point for all partners, with standardized communication protocols and data formats.
A VAN can integrate with a company’s existing systems and processes, providing seamless EDI data exchange with other business systems such as ERP (Enterprise Resource Planning) and CRM (Customer Relationship Management).
Value-added services: Many VANs offer value-added services, such as data translation, mapping, and validation, which can reduce the burden on companies to manage complex EDI data formats and ensure data accuracy.
Maximize your business efficiency with the right VAN provider! Grab your free VAN Buyer's Guide and discover the key features and services that will elevate your EDI transactions to the next level.
Make an informed decision today!
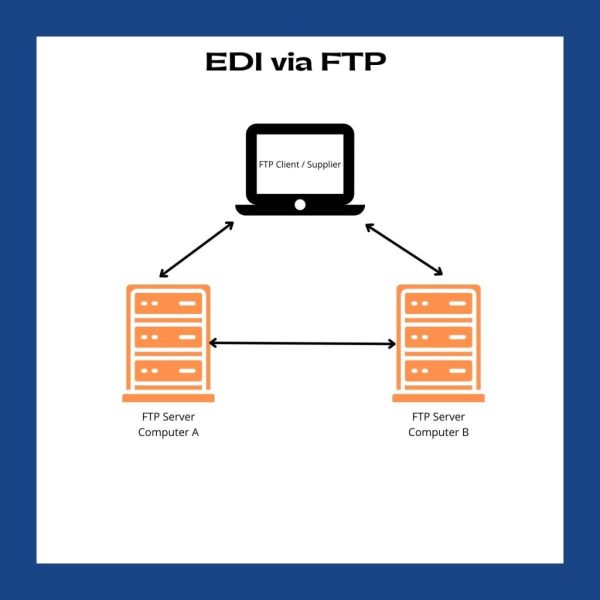
FTP was developed in the early 1970s to allow the transfer of files between computers on different networks. FTP is a standard network protocol used to transfer files from one host to another over the internet. FTP is a simple and reliable method for transmitting EDI files.FTP uses a client-server model, where the client sends requests to the server to download or upload files. The client can be any device such as a personal computer, tablet, or smartphone, while the server is a dedicated computer that stores the files and responds to client requests.
FTP uses two channels, a control channel and a data channel, for transmitting files. The control channel is used to send commands and responses between the client and the server, while the data channel is used to transmit the files themselves. It supports various authentication methods such as usernames and passwords, public and private keys, and SSL/TLS encryption. FTP is widely used to transfer large files between different systems.
FTP is a straightforward protocol that can be easily used by anyone with basic computer skills. The client software is readily available and simple to use, and most web browsers also support FTP.
FTP is supported by most operating systems, including Windows, macOS, Linux, and Unix, as well as many web browsers and mobile devices.
Large file transfer: It can handle large files and can transfer files over a network at high speeds, making it suitable for transferring large amounts of data.
It can be used in different ways, including anonymous file sharing, user authentication, and secure file transfer using encryption protocols such as SSL/TLS.
FTP allows remote access to files stored on a server, enabling users to upload or download files from anywhere in the world, if they have an internet connection.
FTP is a cost-effective method for transferring files, as it does not require expensive software or hardware and can be easily set up using free or open-source software.
FTP is not a secure protocol, and the data being transmitted can be intercepted or modified by third parties. Therefore, it is recommended to use secure variants of FTP such as SFTP (Secure File Transfer Protocol) or FTPS (FTP over SSL/TLS) that provide encryption and authentication to ensure secure file transfer.
FTPS (File Transfer Protocol over SSL/TLS) is a secure variant of FTP (File Transfer Protocol) that provides encryption and authentication for file transfer over a network. FTPS uses SSL/TLS (Secure Sockets Layer/Transport Layer Security) to encrypt the FTP connection, ensuring that the data transmitted between the client and server is protected from unauthorized access or interception.
FTPS can use either explicit or implicit SSL/TLS encryption. In explicit mode, the client establishes a regular FTP connection to the server and then negotiates SSL/TLS encryption. In implicit mode, the FTP connection is encrypted from the beginning, without the need for explicit negotiation. FTPS supports a range of encryption algorithms and key lengths, providing a high level of security for file transfer. It can also support user authentication using various mechanisms, including password-based authentication, public-key authentication, and certificate-based authentication.
FTPS is widely supported by FTP client and server software, making it a popular choice for secure file transfer over a network. However, because FTPS still relies on the FTP protocol, it may not be suitable for all use cases, particularly those that require high-speed or real-time data transfer.

FTPS provides encryption and authentication of data transfer, ensuring that the data transmitted between the client and server is secure and protected from unauthorized access or interception.
FTPS is widely supported by FTP client and server software, making it a popular choice for secure file transfer over a network. This means that companies can leverage existing FTP infrastructure and avoid the cost and complexity of implementing new file transfer protocols.
FTPS supports a range of encryption algorithms and key lengths, providing flexibility in choosing the appropriate level of security for file transfer. It also supports user authentication using various mechanisms, including password-based authentication, public-key authentication, and certificate-based authentication.
It is easy to use and does not require additional software or specialized skills to set up and use.
It provides control over file transfer, including the ability to set permissions, manage access, and track file transfers.
It provides logging and auditing capabilities, allowing organizations to monitor and track file transfer activity for compliance and security purposes.
It can be more complex to set up and configure than non-secure file transfer methods, requiring additional software and technical expertise to implement and manage.
It can be slower than non-secure file transfer methods, particularly when large files are being transferred, due to the overhead of encryption and authentication.
Firewall issues: It can sometimes be blocked by firewalls or network security devices, which may require additional configuration to allow FTPS traffic to pass through.
While FTPS is widely supported, some FTP client and server software may not support FTPS, which could limit compatibility with certain systems or partners.
Cost: Implementing FTPS may require additional hardware or software, and in some cases, may require the purchase of a third-party SSL/TLS certificate.
FTPS requires ongoing management and maintenance, including regular software updates and security patching.
OFTP (Odette File Transfer Protocol) is maintained by the Odette International organization, a non-profit association that promotes the use of standardized electronic messaging and data exchange in the automotive industry. It is a specialized file transfer protocol used primarily in the automotive industry for the exchange of electronic data between manufacturers, suppliers, and other partners.
OFTP uses a client-server architecture, with the client software typically installed at the user’s location and the server software hosted by the partner or service provider and is designed to provide a secure and reliable means of exchanging files over a network, with support for features such as file compression, encryption, error detection, and data integrity checks. OFTP also supports peer-to-peer file transfer between partners who have established a direct connection.
OFTP is widely used by automotive companies and their partners in Europe and other regions and is recognized as a reliable and secure means of exchanging electronic data for supply chain management and other business purposes.
It provides a high level of security for file transfer, with support for encryption, authentication, and data integrity checks. This ensures that data is protected from unauthorized access or interception during transfer.
OFTP is designed to be highly reliable, with features such as error detection and automatic retransmission of failed transfers. This ensures that files are transferred correctly and reliably, even in the face of network or other technical issues.
OFTP is widely used and recognized in the automotive industry, providing a standardized means of exchanging electronic data between partners. This helps to simplify and streamline supply chain management and other business processes.
It supports features such as file compression and batch transfer, allowing for more efficient transfer of large volumes of data.
OFTP can be integrated with other business systems and processes, allowing for seamless and automated transfer of data between partners.
OFTP is designed to be cost-effective, with low overhead and minimal hardware and software requirements.
OFTP can be more complex to set up and configure than non-standardized file transfer methods, requiring additional software and technical expertise to implement and manage.
OFTP is designed to be cost-effective, however, it may still require additional hardware or software, and in some cases, may require the purchase of a license to use the protocol.
OFTP is widely used in the automotive industry, it may not be supported by all partners or service providers. This could limit compatibility with certain systems or partners.
It is mainly used in the automotive industry and may not be suitable for other industries or sectors that have different data exchange needs.
It can sometimes be blocked by firewalls or network security devices, which may require additional configuration to allow OFTP traffic to pass through.
OFTP 2.0 (Odette File Transfer Protocol 2.0) is the latest version of the OFTP protocol, which is designed to provide a secure and reliable means of exchanging electronic data between partners in the automotive industry and other sectors. OFTP 2.0 builds on the features of the original OFTP protocol and introduces several new features.

Supports more advanced encryption algorithms, as well as new authentication mechanisms and key management protocols.
Introduces new features for detecting and correcting errors, such as advanced checksums and real-time acknowledgment of file transfers.
Supports new file types, such as XML and EDIFACT, as well as new compression algorithms and batch transfer options.
Simplified Implementation: Provides a more streamlined implementation process, with support for automatic configuration and simplified testing procedures.
It is based on international standards, ensuring compatibility and interoperability with other systems and protocols.
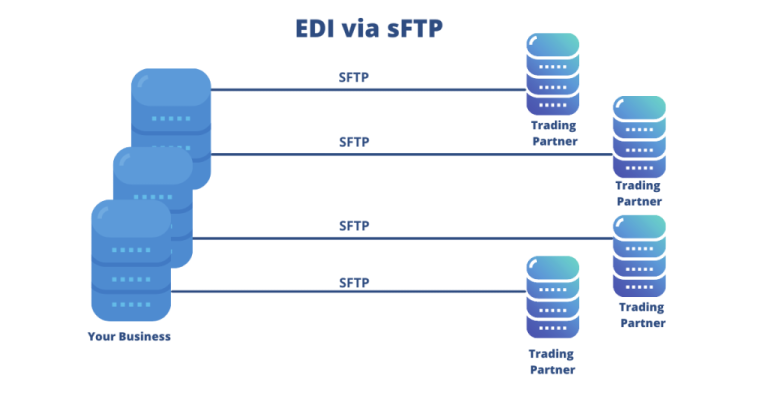
sFTP uses the SSH protocol to establish a secure connection between the client and the server. It provides authentication and encryption of data during transmission, making it more secure than the traditional File Transfer Protocol (FTP). Once the connection is established, sFTP uses a set of commands to perform file operations such as uploading and downloading files, listing directories, and deleting files. sFTP is commonly used for transferring large files and for transferring files securely over the internet.
As the name says, it encrypts all the content within the files during the transfer making them indecipherable to anyone who tries to alter them.
This authentication makes sure the person who is logging in to the server is not an imposter.
These verify the content of the transmitted file to check if the content changed and whether it came from a legit source.
For enabling clients to verify whether the server is actually the server they wanted to connect to.
sFTP encrypts data during transmission, providing a secure and confidential method for transferring files over the internet. It also supports various encryption algorithms, making it difficult for unauthorized users to intercept and access the transmitted data.
sFTP uses SSH protocol to authenticate clients and servers, ensuring that only authorized users can access the files and servers.
sFTP is a reliable protocol that ensures the successful delivery of files. It has built-in error-checking mechanisms that ensure that the files are not corrupted during the transfer process.
sFTP is platform-independent, which means it can run on any operating system, making it easy to integrate with existing systems and applications.
sFTP is designed to handle large files, which can be problematic with other file transfer protocols.
Firewall-friendly: sFTP is firewall-friendly, as it uses a single port for data transfer, making it easier to configure and secure.
sFTP can be more complex to set up and use than traditional FTP, especially for users who are not familiar with SSH and encryption protocols.
Because sFTP encrypts data during transmission, it can be slower than traditional FTP for transferring large files, especially on older hardware or over slower connections.
While sFTP is widely supported by many operating systems and file transfer clients, it may not be supported by all legacy or proprietary systems.
sFTP requires administration and maintenance of the SSH server and client software, which may require additional resources and technical expertise.
Compatibility: Some older versions of SSH and sFTP clients may not be compatible with newer versions of SSH servers, which can cause compatibility issues when transferring files.
The AS1 (Applicability Statement 1) protocol was first published in March 2002 as part of the Electronic Data Interchange – Internet Integration (EDIINT) specifications by the Internet Engineering Task Force (IETF). It is a standard protocol used for the secure and reliable transfer of electronic data over the internet using email protocols. Provides a secure and reliable method for businesses to exchange electronic documents, such as invoices, purchase orders, and other business-related documents, between different organizations.
AS1 uses the Simple Mail Transfer Protocol (SMTP) for message transport, and the Secure/Multipurpose Internet Mail Extensions (S/MIME) and the Multipurpose Internet Mail Extensions (MIME) for message security and integrity. It also uses digital certificates to authenticate senders and receivers of messages and ensure the confidentiality and integrity of the data being transmitted.
AS1 is often used in conjunction with other protocols such as AS2 and AS3 to provide a complete and secure system for exchanging electronic data between businesses.
sFTP encrypts data during transmission, providing a secure and confidential method for transferring files over the internet. It also supports various encryption algorithms, making it difficult for unauthorized users to intercept and access the transmitted data.
sFTP uses SSH protocol to authenticate clients and servers, ensuring that only authorized users can access the files and servers.
sFTP is a reliable protocol that ensures the successful delivery of files. It has built-in error-checking mechanisms that ensure that the files are not corrupted during the transfer process.
sFTP is platform-independent, which means it can run on any operating system, making it easy to integrate with existing systems and applications.
sFTP is designed to handle large files, which can be problematic with other file transfer protocols.
Firewall-friendly: sFTP is firewall-friendly, as it uses a single port for data transfer, making it easier to configure and secure.
sFTP can be more complex to set up and use than traditional FTP, especially for users who are not familiar with SSH and encryption protocols.
Because sFTP encrypts data during transmission, it can be slower than traditional FTP for transferring large files, especially on older hardware or over slower connections.
While sFTP is widely supported by many operating systems and file transfer clients, it may not be supported by all legacy or proprietary systems.
sFTP requires administration and maintenance of the SSH server and client software, which may require additional resources and technical expertise.
Compatibility: Some older versions of SSH and sFTP clients may not be compatible with newer versions of SSH servers, which can cause compatibility issues when transferring files.
100% EDI Compliance Guaranteed!
AS2 (Applicability Statement 2) provides a secure and reliable way to exchange data between trading partners, using encryption and digital signatures to protect the confidentiality, integrity, and authenticity of the data being transmitted. It is typically used for the exchange of EDI transactions but can also be used for other types of data transfer.
A simple AS2 setup involves two computers – a client and a server – connecting in a point-to-point manner via the Web. Sending EDI documents via AS2 requires the receiving organization’s server to be always ‘listening”. Similar to a call to a phone without an answering machine, the message will be missed if the AS2 server is not available. As a result of this high availability requirement, many businesses prefer to use an EDI provider such as Commport to provide their AS2 connectivity.
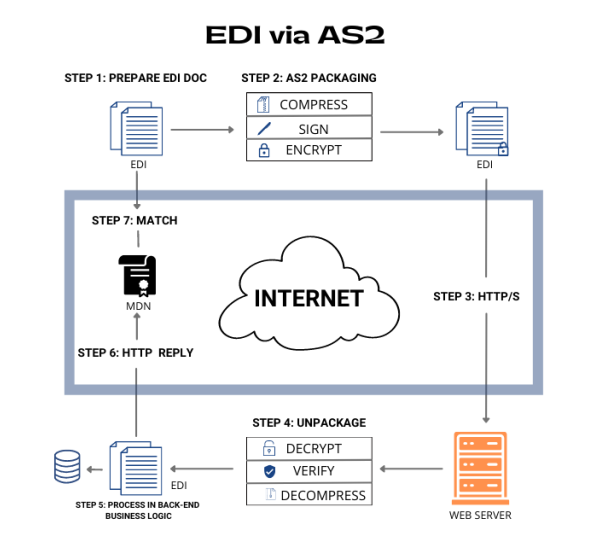
AS2 uses encryption and digital signatures to protect the data being transmitted, ensuring that it cannot be intercepted or tampered with by unauthorized parties.
AS2 provides a reliable and error-free way to exchange data between trading partners, with built-in error handling and message acknowledgment mechanisms.
The data is encrypted, and the identity of the sender and the integrity of the payload are ensured using pre-established digital certificates that are validated upon each connection.
Automation: AS2 enables the automation of many business processes, reducing the need for manual data entry and increasing efficiency.
AS2 is a cost-effective alternative to traditional EDI methods, which often require dedicated communication lines and expensive software.
AS2 can be more complex to set up and maintain than other data transfer methods, which may require technical expertise and ongoing support.
Network Connectivity: AS2 requires both the sender and receiver to have a reliable and stable internet connection, which may not be available in all locations or under all circumstances.
AS2 has a maximum message size limitation, typically around 2GB, which may not be sufficient for some types of data transfer.
Scalability: While AS2 can be used to exchange data with multiple trading partners, it may not be as scalable as other protocols for larger networks of partners.
AS2 requires both the sender and receiver to use compatible software and adhere to the same standards, which may not always be the case, leading to compatibility issues.
Setting up and maintaining an AS2 infrastructure may require some initial investment, such as software licensing fees, hardware upgrades, and ongoing maintenance costs.
Unlock the full potential of your supply chain with our comprehensive EDI Buyer's Guide — your first step towards seamless, efficient, and error-free transactions
AS3 (Applicability Statement 3) is a protocol that was developed by the Internet Engineering Task Force (IETF) for secure and reliable messaging over FTP (File Transfer Protocol). It is based on the secure version of FTP (FTPS) and uses S/MIME (Secure/Multipurpose Internet Mail Extensions) for message security.

AS3 uses S/MIME encryption and digital signatures to protect the confidentiality, integrity, and authenticity of the messages being transmitted.
AS3 provides reliable delivery of messages using MDN (Message Disposition Notification) receipts, similar to AS2.
AS3 is designed to work with existing FTP infrastructure and applications, making it a good choice for industries that heavily invest in FTP scripting, applications, and security.
Push/Pull Model: AS3 supports both push and pull message delivery, allowing for greater flexibility in how messages are sent and received.
No Persistent Connection
Unlike AS2, AS3 does not require a persistent connection for the listener, making it easier to implement and manage.
AS3 can be more complex to set up and maintain than other messaging protocols, particularly if the organization does not already have a strong FTP infrastructure and expertise.
Limited Adoption: AS3 has not been widely adopted compared to other messaging protocols like AS2, which may limit its interoperability with trading partners.
AS3 has a maximum message size limitation, typically around 2GB, which may not be sufficient for some types of data transfer.
AS3 requires both the sender and receiver to use compatible software and adhere to the same standards, which may not always be the case, leading to compatibility issues.
Setting up and maintaining an AS3 infrastructure may require some initial investment, such as software licensing fees, hardware upgrades, and ongoing maintenance costs.
AS4 (Applicability Statement 4) was developed by the sub-committee of the OASIS ebXML messaging services technical committee. AS4 is a secure B2B (Business to Business) document exchange protocol that is designed to use web services to facilitate the exchange of messages between trading partners. AS4 is still in its draft definition format.

AS4 provides end-to-end message security using digital signatures and encryption, ensuring that messages cannot be intercepted or tampered with during transmission.
Reliability: AS4 ensures reliable message delivery using message receipts and acknowledgments, allowing trading partners to confirm that messages have been successfully received and processed.
AS4 is designed to be interoperable with a wide range of web services platforms, making it easy for companies to exchange messages with their trading partners regardless of the platforms they use.
AS4 provides a high degree of flexibility in terms of message format, allowing companies to exchange a wide range of B2B documents.
AS4 can be easily integrated with existing Service-Oriented Architecture (SOA) platforms, making it a good option for companies that have already invested in SOA-based solutions.
AS4 is highly scalable, making it suitable for use in large-scale B2B document exchange environments.
AS4 can be more complex to set up and configure than some other B2B messaging protocols.
Standardization: AS4 is still in its draft definition format, which means that some aspects of the protocol may change as it evolves.
While AS4 is designed to be interoperable with a wide range of web services platforms, there may still be compatibility issues that need to be addressed when exchanging messages with trading partners.
Setting up and maintaining an AS4 infrastructure may require some initial investment, such as software licensing fees, hardware upgrades, and ongoing maintenance costs.
ebMS (Electronic Business Message Service) developed by OASIS (Organization for the Advancement of Structured Information Standards) and is also known as ebXML Messaging. ebMS is a messaging protocol that is used for secure and reliable exchange of business documents and messages between trading partners.
ebMS is designed to support B2B (business-to-business) messaging and is based on the XML (Extensible Markup Language) standard. It provides a framework for exchanging messages that includes features such as message packaging, routing, security, and reliability.

ebMS provides end-to-end security for messages using digital signatures and encryption.
ebMS provides reliable message delivery using message receipts and acknowledgments.
ebMS is designed to be interoperable with a wide range of messaging systems and platforms.
ebMS supports a wide range of message formats, including XML, binary, and text.
ebMS is highly scalable, making it suitable for use in large-scale B2B document exchange environments.
Implementing and configuring ebMS can be complex, especially for organizations that are not familiar with the protocol or have limited IT resources.
Implementing and maintaining an ebMS infrastructure may require a significant investment in terms of software licensing fees, hardware upgrades, and ongoing maintenance costs.
Although ebMS is designed to be interoperable with a wide range of messaging systems and platforms, there may still be compatibility issues that need to be addressed when exchanging messages with trading partners.
Organizations that are new to ebMS may need to invest time and resources into learning the protocol, which could slow down the adoption process.
While ebMS is a widely adopted and trusted messaging protocol, it is still a standard that is subject to change over time, which could lead to compatibility issues or the need for updates to existing systems.
REST (Representational State Transfer) API, also known as RESTful API, is a type of API (Application Programming Interface) that is designed to be used with web services. It is a popular architectural style for building web services, and it is based on the HTTP (Hypertext Transfer Protocol) protocol.
REST API is designed to allow clients to access and manipulate web resources using a set of well-defined operations, including GET, POST, PUT, and DELETE. These operations correspond to the CRUD (Create, Read, Update, and Delete) operations commonly used in database applications.
REST API is a powerful tool for building web services that can be used across different platforms and programming languages. It is widely used in modern web applications and is a key component of the web services architecture.
REST API can help to facilitate EDI (Electronic Data Interchange) by providing a modern and flexible way to exchange business documents between trading partners. Traditional EDI systems rely on proprietary protocols and complex data formats that can be difficult and expensive to implement and maintain.
By using REST API for EDI, trading partners can leverage the benefits of web services and the HTTP protocol to exchange data in a more efficient and standardized way. REST API can also provide a simpler and more flexible approach to data mapping and transformation, allowing trading partners to exchange data in a variety of formats and protocols.
One of the key advantages of REST API for EDI is that it can be easily integrated with other systems and applications, including ERP (Enterprise Resource Planning) systems, CRM (Customer Relationship Management) systems, and other business software. This makes it easier to automate business processes and reduce manual data entry and processing.
REST API can also help to improve the speed and accuracy of EDI transactions, as well as increase visibility into the supply chain. With real-time data exchange and tracking, trading partners can more effectively manage inventory levels, production schedules, and customer orders.

The client and server are separate entities that communicate with each other using standard HTTP methods.
The server does not store any client context between requests, which simplifies the server design and allows for greater scalability.
Responses to client requests can be cached to improve performance.
REST API allows for the use of intermediaries, such as proxies and gateways, to improve scalability and security.
REST API defines a uniform interface between the client and server, which makes it easier to develop and maintain web services.
RESTful APIs are built on HTTP protocol, which can lead to challenges with scalability and reliability when scaling up to handle high-volume requests.
RESTful APIs are not ideal for more complex operations such as transactions that require multiple steps or multi-object queries.
RESTful APIs rely on HTTP for authentication and encryption, which can be vulnerable to certain attacks like session hijacking, cross-site scripting, and cross-site request forgery.
There is no standard format or structure for RESTful APIs, making it difficult to implement them in a uniform manner across different platforms and programming languages.
RESTful APIs can suffer from performance issues when handling large or complex datasets, as they can require multiple requests to retrieve all the necessary data.
RESTful APIs are stateless, which means they don’t store any session information, and each request is treated as a new request. This can be a challenge when dealing with applications that require state management.
Cloud-based EDI is a cloud-based EDI solution that makes connecting and doing EDI with your valued customers fast and easy. Start doing EDI within hours with any of our many supporting grocers and retailers.
The ease of rolling out a Web EDI solution facilitates the participation of all your business partners. This can be especially beneficial when working with partners where IT and EDI skills are limited. Companies are not required to install any EDI software or manage a complex EDI environment.
Even smaller or mid-sized vendors need to be compliant with their large retail customers. As a low-cost option, our Web EDI solution enables you to get up and running with very little investment required. All you need is an Internet connection and a web browser and you can begin exchanging EDI with your trading partners today.
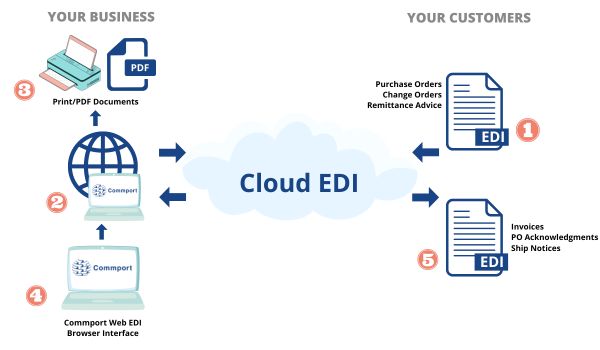
Web EDI eliminates the need for expensive hardware, software, and dedicated communication lines, resulting in significant cost savings for businesses.
Web EDI is easy to set up and use, with minimal training required for end-users. This makes it accessible for small and medium-sized businesses that may not have the resources to implement traditional EDI solutions.
Web EDI enables real-time transactions, allowing businesses to process orders, invoices, and other transactions in near real-time.
Web EDI reduces the risk of errors that can occur when data is manually entered, leading to improved accuracy in transactions and reducing the need for manual corrections.
Web EDI streamlines business processes, allowing businesses to process transactions faster, reduce processing times, and improve overall efficiency.
Web EDI can easily scale up or down based on business needs, making it an ideal solution for businesses of all sizes.
Enhanced customer service: Web EDI enables businesses to respond to customer requests faster and more accurately, leading to improved customer satisfaction and loyalty.
Mobile EDI is still in its very early days of development. Many companies are developing EDI apps that can help facilitate the transfer of electronic data interchange (EDI) data between business partners using your smartphone or tablet. Just like web EDI, you can start exchanging EDI right from your mobile device and access it 24/7 on the go. You can do business were ever you go.

Yes, businesses can use multiple protocols to meet diverse partner requirements. An advanced EDI system can support various protocols, allowing businesses to connect with different partners seamlessly, regardless of each partner’s preferred method.
Key factors include data security requirements, regulatory compliance, compatibility with trading partners, transfer speed, and cost. Businesses should select a protocol that meets industry standards, offers sufficient security, and aligns with partner preferences.
SFTP (Secure File Transfer Protocol) is an encrypted version of FTP (File Transfer Protocol). While FTP allows basic file transfers, SFTP ensures data is encrypted during transmission, making it more secure and suitable for sensitive EDI exchanges.
AS2 is a popular EDI communication protocol that allows secure and reliable transmission of EDI documents over the internet. It provides encryption and digital signatures, making it a preferred choice for industries that require high data security, such as retail and healthcare.
Common EDI communication protocols include AS2 (Applicability Statement 2), FTP (File Transfer Protocol), SFTP (Secure File Transfer Protocol), HTTPS (Hypertext Transfer Protocol Secure), and X.400. Each protocol has its own security features, making them suitable for various industries and business needs.